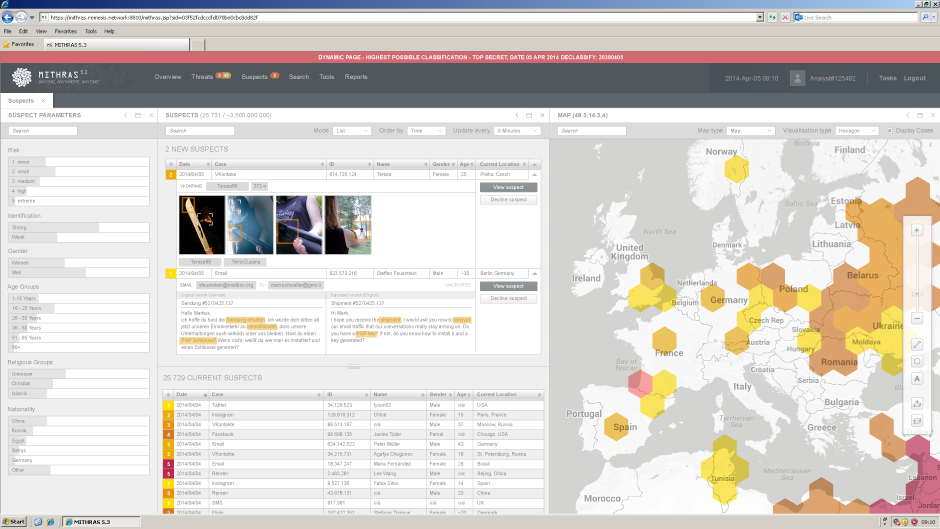
The overview summarizes the current suspects. Every person, who acts differently in the agency’s perspective, like searching for certain topics on Google, could be a suspect. New suspects, which the system filtered out being suspicious, are highlighted and can further be analyzed being potentially dangerous. The software allows the analyst to sort, filter, and search. A map gives the analyst an additional overview of the geographical risk areas.

The profile gives an overview of a certain person. It is used to get a first impression of a suspect and can turn the suspect into a possible target. The personal data consists of name, age, nationality, physical characteristics, current location and agency specific information like number of collected online and telephone data.

'Media' allows the analyst to see and analyze the content of different social networks and internet services. Using the example of Instagram, the analyst receives a first glimpse of the suspects' daily life. The content of the most pictures seem to be trivial, but they contain important metadata, like the place where the picture was taken and with whom.

The exchange of messages via SMS or email forms a large part of our global communication. The collection of these channels exposes worldwide social relations and the everyday behavior of humans. When and how often we communicate with a person could give an agency information about our next purchase, illness or possible terrorist attack. The analyst uses the collected emails to find interesting events in the subjects' past and to analyze its communication behavior.

Web analysis tools show an overview of all visited websites. The high number of pages and their content form a detailed image of the suspects' interests. The picture is formed by statistical analysis of the most visited pages, their risk factors and their legal information. In addition, search functions and timeline allow goal-oriented research in the past of the suspect.
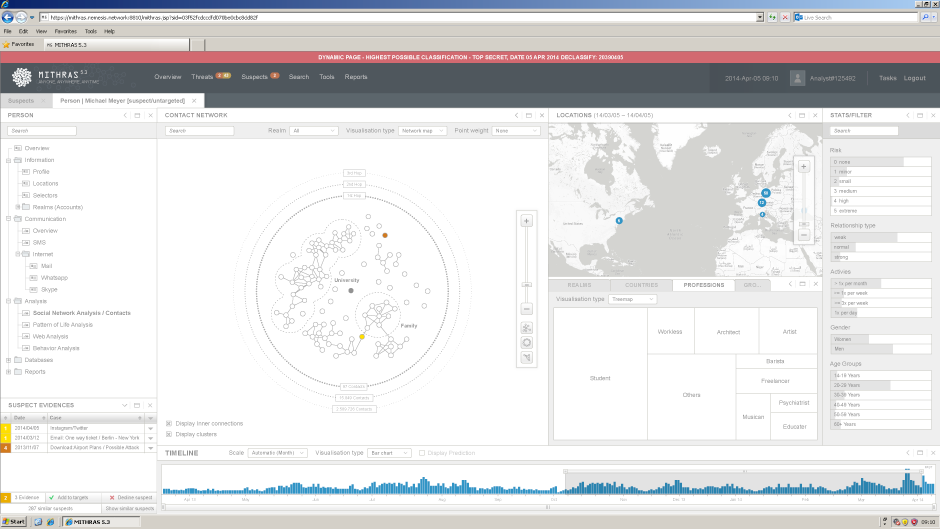
The contacts show the analyst an overview of the suspect's social networks: with whom the person most frequently communicated or met and gives him further information about the suspect's life, its contacts and is able to sort them according to specific criteria, such as gender, age, contact number and their connection. In addition, a map and several diagrams give more information about the suspect's contacts, such as the location or their profession.

The localization of a suspect is an important part of mass surveillance. The agencies are collecting this data for example from mobile phones. In this project the application gives the analyst not only the location of a suspect and its contact. The analyst also gets an overview of all located and identified persons. That means everybody, who is in the nearest distance of the suspect, can become a suspect too. These people can be filtered according to demographic criteria such as age or nationality. In addition, all media and messages that have emerged in this area can be queried and displayed. The analyst gets a bird's eye view of the suspect's digital world and their contacts.